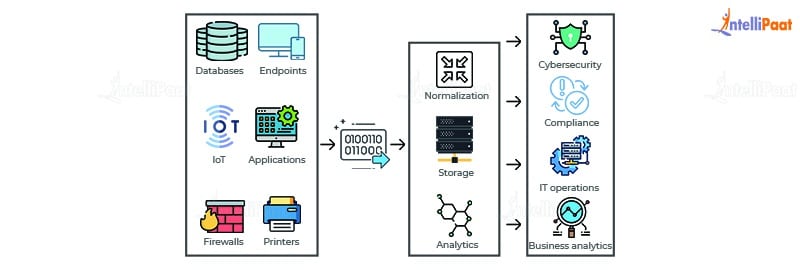
Security Information and Event Management, popularly known as SIEM system, is critical to any cybersecurity strategy. It helps protect against threats and provides visibility into your entire IT environment.
SIEM is a security control system that integrates the two components of security event management (SEM) and security information management (SIM). This technology gathers event logs from a range of sources. By identifying activity that deviates from the norm with real-time analysis, and takes appropriate action.
How Does SIEM work?
SIEM software is used to gather and examine massive volumes of data from users, servers, and devices within an organization in real-time. Enabling security teams to promptly detect and stop threats. SIEM tools operate according to already established procedures to facilitate the way security teams define threats and send out alerts.
What are the Benefit of SIEM?
SIEM can be a complex solution that requires experienced staff to implement and fine-tune. Before investing, it’s essential to understand its key benefits.
Improved Detection
By the way, what is SIEM? A SIEM is a powerful tool that can alert you to potential environmental threats. It can also help you meet various compliance requirements, including PCI, NERC, PII, and HIPAA. The best way to get the most out of an SIEM is to properly tune it to your network and environment.
Tuning your SIEM involves establishing the appropriate rules and thresholds to differentiate normal and abnormal network activity. This can be accomplished through simple rules that correlate one event with another or more complex correlations of different events, such as a compromised login, a large file transfer, and a location change.
These models can significantly improve visibility into your network and detect various threats, even ones outside of the perimeter, like remote user access to SaaS applications and devices or attacks carried out from the cloud. This lets your security team focus on the most dangerous incidents and prioritize the threats threatening your business. This helps you get the most value out of your SIEM and reduces the time you spend dealing with unnecessary alarms.
Reduced False Positives
SIEM can churn out too many false positive alerts unless it is configured correctly and tuned to the security needs of your organization. This can bog down analysts, creating a productivity drain that reduces their ability to detect real threats and mitigate them quickly.
This is especially true if the system has to use configuration management data to solve the problem. You can first try to understand the typical activity in your environment and then identify deviations from that baseline. UEBA or user and entity behavior analytics can help remove these annoying false positives.
This is possible if you configure the rules correctly, which takes time to set up properly (so the solution knows what is typical for your environment). If you configure these rules right, it will be possible for the software to distinguish between legitimate security events and false positives so that it will trigger too many alerts. It’s also essential to enable only the rules necessary in your environment, as leaving every default rule allowed can cause alert fatigue. This is a common mistake.
Better Compliance
With a SIEM program, you can monitor all devices and applications—including those of remote employees—from one central location. This active monitoring can help you identify and correct cyberattacks in far less time than if you were manually monitoring each device.
SIEM also enables you to create custom rules, alerts, and dashboards tailored to your security needs. This helps your analysts get the needed information without being overwhelmed by too many false positives.
A good SIEM program uses models rather than correlation rules, making it more likely to recognize real threats. Which can prevent attackers from taking advantage of the system. Models require multiple events to occur, like a user logging in from a different location or carrying out a large file transfer, to trigger an alert.
The benefits of SIEM solutions are numerous, but implementing and maintaining one requires more work. It also requires the talent of experienced IT environments and security teams. Managed SIEM services eliminate the stress of deploying, managing, and monitoring an SIEM platform—and they can also save your organization money by eliminating the need for you to invest in software and hardware.
Enhanced Visibility
With the SIEM system, security teams can get a real-time bird’s-eye view of what is happening on their network. This visibility eliminates blind spots, making detecting and responding to attacks much easier.
With the rise of remote workforces, organizations need to be able to mitigate risks wherever digital assets are accessed. A SIEM solution can help to do this by providing visibility into all network activity – regardless of the device, application, or service the activity is associated with.
The other benefit of SIEM visibility is reducing the time it takes to identify threats and take action. This is crucial as the longer an attack goes unnoticed, the more damage it can cause.
Alongside correlation rules, some next-gen SIEM solutions include user and entity behavior analytics (UEBA) that automatically detect suspicious behavior patterns and alert the security team. This can be extremely useful for detecting DDoS attacks and file integrity breaches that could indicate an attacker at work.
Increased Security
When correctly configured and tuned to fit your environment, an SIEM solution can surface indicators of a threat that could lead to a breach. This is made possible through correlation and analysis, allowing security staff to identify malicious activity promptly.
The History of Security Information and Event Management?
SIEM solutions have been around for decades, with varying degrees of functionality based on which product or vendor you choose.
Gartner analysts Mark Nicolett and Amrit Williams coined the term SIEM in 2005. First-generation SIEM focused mainly on traditional log collection. The next generation of SIEM platforms focused on security events based on triggers from tools such as antivirus, firewalls, and intrusion detection systems (IDS).
Many SIEM systems now incorporate the capabilities of user and entity behavior analytics and security orchestration, automation, and response. Which makes them full-fledged tools to help protect your organization against cyberattacks. Combined with powerful event correlation and advanced analytics, these solutions can significantly improve the mean time to detect and the mean time to respond for IT security teams. By offloading manual workflows, they free up the time and resources needed to address the most severe threats.
You must be logged in to post a comment.