The ‘wonder’ Apple technology has ensured that it’s thief will not go uncaught. Last week saw the house of Mr. Tunde Makhinde, a Lagos based Nigerian visited by some robbers who took his iPad among other things. Little did they know that the iPad will eventually turn out to be the nail to their coffin: The tech whiz had activated the tracking device on his iPad, and within a matter of days, had gone with law enforcement agents to catch the thieves red handed.
Recently, an amazing app, Find my iphone, was used to track down a stolen iPad and the man who allegedly took it from underneath a family’s Christmas tree in the US. The victim on the ‘Find my iPhone’ app that sends out a signal to the device.Using his computer, the victim was then able to locate the iPad on a map, and alerted police to its whereabouts – just a few houses away.
Even the burglar who broke into Steve Jobs’ house was caught last year two weeks after the crime thanks to the technology in one of the late Apple founder’s own inventions. He might never have been caught if he hadn’t logged onto iTunes on one of Jobs’ personal iPads. Investigators say they were tipped off about the perpetrator when one of the stolen devices connected to Apple servers.
What if…?
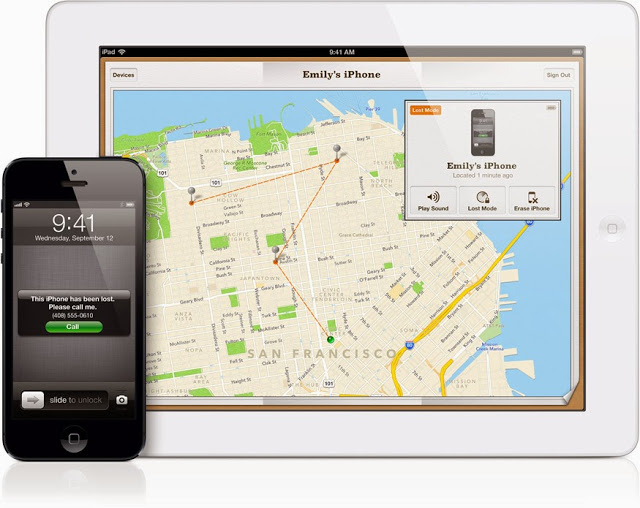
‘But I am no tech whiz!” you might say. That doesn’t matter. How smart would smart technology be if it can’t holler at its owner when it gets stolen? There are simple ways to be two steps ahead of the thief. The ‘Find My iPhone’ application can be used if an Apple device is stolen or misplaced. It does not come installed but can be downloaded for free.
The user then signs in with their unique Apple ID.a device goes missing, the owner can activate the app on a computer. Signals ‘ping’ the device and its whereabouts can be seen on a map online.can then choose to display a message on its screen, play a sound for two minutes at full volume, lock the device or erase all of its data.can be used on iPhones, iPads, Apple computers and iPods.
iOS 7 includes a new feature called Activation Lock, which makes it more difficult for anyone to use or sell your iPhone, iPad, or iPod touch once it’s gone missing or has been stolen. And it starts working the moment you turn on Find My iPhone in iOS 7. Turning off Find My iPhone or erasing your device requires your Apple ID and password. And your Apple ID and password are required before anyone can reactivate it.
But what happens if you find your device on a location you can’t reach? Go for second best-initiate a remote wipe to delete your personal data and restore your iPhone, iPad, iPod touch, or Mac to its factory settings. With iOS 7, Find My iPhone can continue to display your custom message, even after your device has been erased. And if you do retrieve your device, you can restore it from your iCloud backup. iCloud is not just for backup, it can help you find your apple device on the map. If one of your Apple devices goes missing, iCloud can help you figure out where it is. Just sign in at iCloud.com or use the Find My iPhone app to see your missing iPhone, iPad, iPod touch, or Mac on a map.