Recently recognized as the 10th fastest growing company in the IT sector by Inc. Magazine, Arvixe has gradually made its name in the web development world.
Notably, the Arvixe Web Hosting Company has been the most recommended hosts, offering reliable but affordable hosting plan for Oxwall and WordPress hosting. It is therefore no surprise at the number of contacts I receive everyday asking for guides on how to setup their Arvixe hosting account.
Some Unique Features of Arvixe

Arvixe is largely popular with WordPress users partly because it fully adheres to all WordPress hosting system requirements (basically the same story with every other cms out there). Also the compatibility issues with Joomla 3.0 has been fixed as it is now fully compatible with Joomla 3.0!
The prices are quite affordable, here at EWT we have rounded up a few coupon codes that will enable you to purchase cheap hosting services from Arvixe (as low as $0.01 for the first month and 20% discount for every purchase) you may check it out at the Arvixe coupon page.
Less I forget, it is unlimited data transfer, 99% uptime, unlimited disk space, 1 free domain name for life, you know them right? Without wasting much time lets go down to the main business:
Getting Started
The moment you click here should take you to the Arvixe landing page. Kindly follow the steps below to setup your hosting account.
- Domain Search: On the top-right hand side of your screen, you will see a box label ‘Domain Search’. This is where you look up domain names. Kindly type a domain name (e.g. www.yourwebsitereg) into the box and select a TLD (e.g. .com, .net, .org etc) from the dropdown just beside the input box.
Now click on the ‘Check Availability’ button. Please Note that the same method is applicable for both new domain registration and domain name transfer. The next page contains a list of TLD available for registration in regards to your search. If a domain name is available for registration, a button is placed just under it, you can simply click on this button to register the domain name. A
button is placed just under it, you can simply click on this button to register the domain name. A  button is used to denote that a TLD is neither available for new registration or for domain transfer.
button is used to denote that a TLD is neither available for new registration or for domain transfer. - Domain Transfer: A
 button is placed below a TLD to signify that the domain name is not available for new registration but can be transferred to the Arvixe hosting account. You can also use this option if you are trying to transfer your domain name from a different domain name provider to Arvixe (Remember that Arvixe allows you to register 1 free domain name for life), so it’s quite a tempting offer for everyone.
button is placed below a TLD to signify that the domain name is not available for new registration but can be transferred to the Arvixe hosting account. You can also use this option if you are trying to transfer your domain name from a different domain name provider to Arvixe (Remember that Arvixe allows you to register 1 free domain name for life), so it’s quite a tempting offer for everyone. - Now when you are done by selecting the options that fits your motives, you can proceed to the billing center by clicking on the next button at the top-right of the screen.
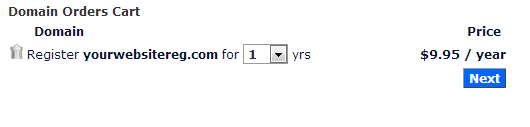
- Fill the required information on the billing form and click the next button.
- Select your hosting plan, eg. Personal Class, Personal Class Pro etc.
- From the drop down option choose a your model of payment e.g. 2years, 1year or payment on a monthly basis. Then click on Add to Cart to continue.
- The next page that comes up is where you select the services your opting for. You can choose whether you want to register a new domain name, transfer a domain name to Arvixe or simply point your domain name to Arvixe hosting. To do that, simply select the radio button corresponding to what you want to do and fill in your login details. Check the auto renew box if you want your account to be automatically renewed after expiration. Finally, click on next.
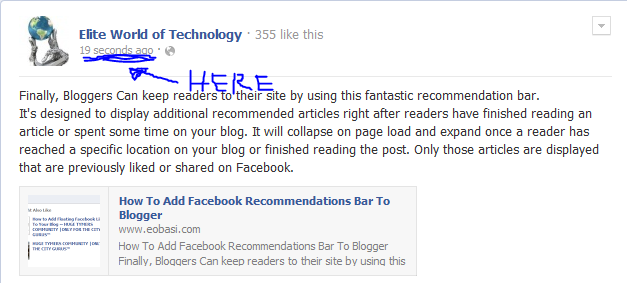
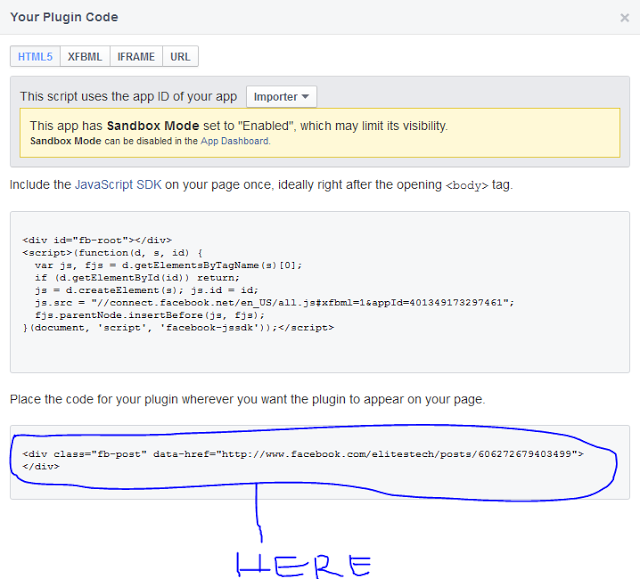
- Using Coupons: The coupon codes one way or the other minimize the cost of transaction for your hosting account. (Here at EWT we generate lots of coupon codes that offers you up to 20% discount for every purchase you make on Arvixe. You may check out this page for free Arvixe coupon codes). To use Promo/Coupon Code, paste your coupon code in the box at the top-right hand side of the screen and click use
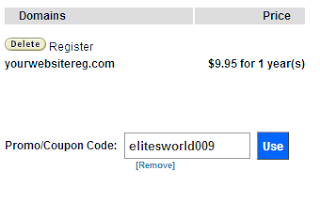 Note that to use a coupon code, you need to do this before the above step (before clicking next in the previous step).
Note that to use a coupon code, you need to do this before the above step (before clicking next in the previous step).
Some Problems you are Likely to Encounter while Signing Up
“Good things” they said, “don’t come so easy”, as a young man I don’t think I’d totally agree with that saying but creating an Arvixe account doesn’t come on a silver platter. You are bound to get stuck on the way and that is why I’m writing this step to step guide.
You are a Fraud
If you have just completed the above step and receive a welcome message telling you that your account is a fraud. Well, don’t panic over this, as Arvixe tends to dislodge any registration from some countries outside the US. In this state your account status should be showing ‘Unverified’, all you have to do is to verify your account.
How to Verify your Arvixe Account
In Arvixe, you can verify your account regardless if you have purchased a plan already or not. This to ensures that there is no interruption of service most especially if you have already set up your website after receiving your Hosting Account Information via e-mail.
Arvixe Verification Process
There are two types of verification. The first one is Manual. Manual verification requires a customer to submit a scanned copy of one valid ID and a proof of payment.
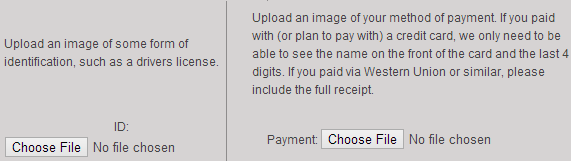
Manual Verification For credit card payments, a scanned copy of the front side of the card showing the name and the last four-digits are required. The rest should be masked for security (recommended) If you paid using other payment methods such as PayPal, Skrill, or Google Checkout, you may chat with the billing support to ask the required documents for verification. They can help you verify your account quickly. Alternatively, you can verify your account over the phone. Phone verification is the easiest way to validate an account. The procedure is automated. You just need to provide a working phone number then Arvixe will call it. A unique verification code will be provided at the same time. Key-in the code within the allowed time to complete the verification.
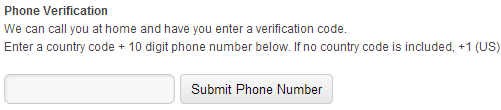
Phone Verification To verify your account through the phone, go to Arvixe Verification page. This link will be provided to you via email after creating a billing account. If the code is correct, the automated voice prompt will confirm the account activation then ends the call immediately. If not, you can initiate phone verification again and a new code will be provided. The same phone number can be used. The code will appear in the top portion of the Arvixe Verification webpage so keep an eye on the page when you received the call. ‘That account is already verified.’ will show once verification is completed. Refresh the page to see the confirmation. Credit:starrguide.com
If you are signing up from Nigeria, just give them a scan copy of your Voter’s Card/National ID/Driving Licence and a scan copy of your Visa card. That should be all.
If you are transfering to Arvixe, the whole process should take less than 48hours to complete. New registrars can proceed to their cpanel (your cpanel details will be mailed to you) and initiate the awesome!
Thanks for reading and Happy Sharing! Remember to contact the arvixe support should you ecounter any problem (those guys are ever ready to help out), if you have any question, contribution or suggestion feel free to use the comment box below, Nice to have you in our blog today 🙂


 Currently, we are on the edge of a new digital paradigm, where the abilities of our machinery are beginning to outshine our own.
Currently, we are on the edge of a new digital paradigm, where the abilities of our machinery are beginning to outshine our own.












 As interesting as the reliability figures was the level of improvement shown by these recent versions, some only months or even weeks old.
As interesting as the reliability figures was the level of improvement shown by these recent versions, some only months or even weeks old.
 Ballmer, however, has recently refocused Microsoft in order to drag the PC stalwart into the faster-moving mobile age, initiating drastic sea changes such as the device-spanning
Ballmer, however, has recently refocused Microsoft in order to drag the PC stalwart into the faster-moving mobile age, initiating drastic sea changes such as the device-spanning 











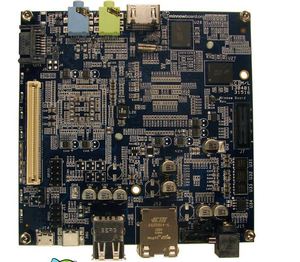 The PC, called the MinnowBoard (shown above), is basically a motherboard with no casing around it. It was codeveloped by Intel and CircuitCo Electronics, a company that specializes in open-source motherboards, and went on sale this month for $199 from a handful of retailers.
The PC, called the MinnowBoard (shown above), is basically a motherboard with no casing around it. It was codeveloped by Intel and CircuitCo Electronics, a company that specializes in open-source motherboards, and went on sale this month for $199 from a handful of retailers.